From AWS IAM fundamentals to broader cloud and research driven security thinking
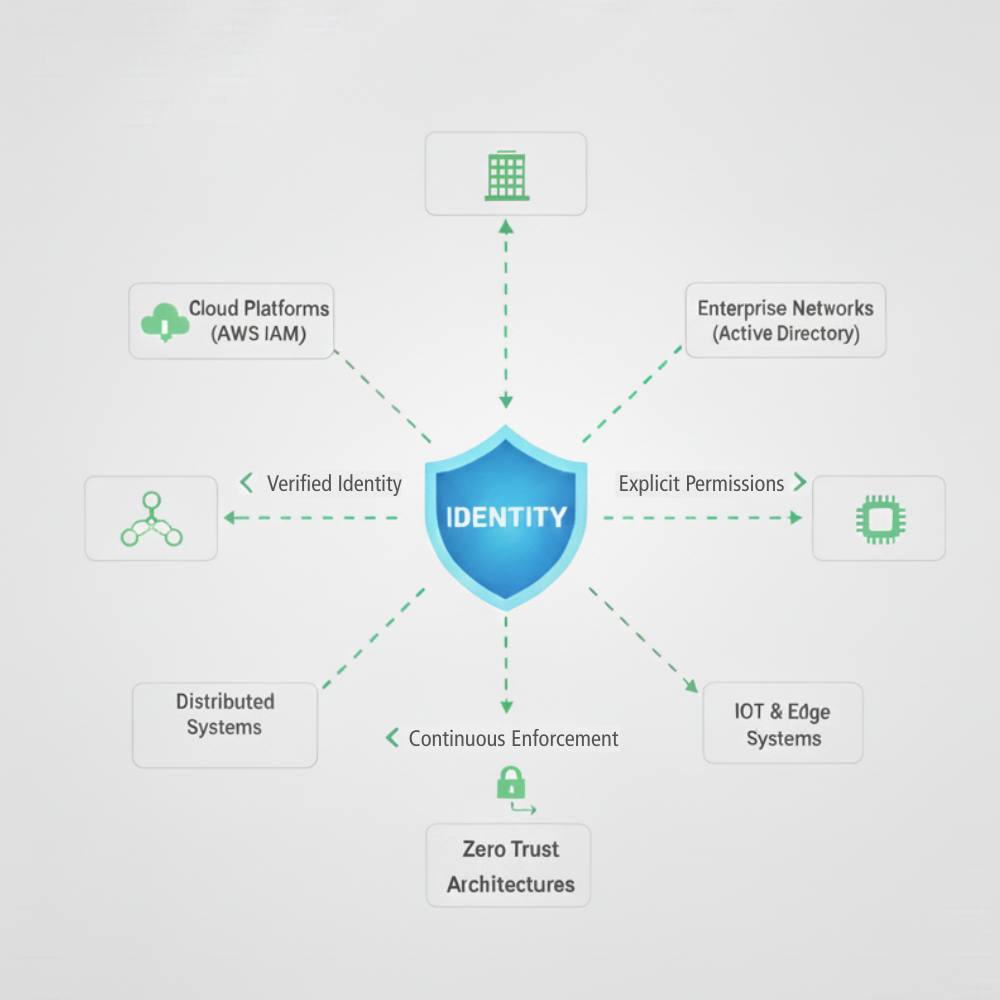
Identity and Access Management (IAM) sits at the core of how modern cloud platforms enforce trust, least privilege, and accountability at scale. While the tooling and examples discussed here are drawn from Amazon Web Services, the underlying ideas extend far beyond a single provider and connect directly to cloud networking, distributed systems, and security research.
Rather than treating IAM as a narrow service offering, this post looks at it as a foundational security model. The same principles that govern IAM in the cloud also appear in enterprise networks, zero trust architectures, and constrained environments such as IoT and edge systems.
What follows is a structured discussion of core IAM concepts, framed in a way that highlights their relevance across modern computing environments.
Identity as the new perimeter
Traditional enterprise security relied heavily on a well defined network boundary. Firewalls, VPNs, and internal segmentation controlled who could access what. In cloud and distributed systems, that boundary is no longer sufficient.
IAM shifts the focus from where a request originates, to who or what is making the request.
In AWS, every action is authenticated and authorized through IAM. Conceptually, this aligns with identity centric security models used across cloud providers and enterprise platforms.
Key idea
Access decisions should be based on verified identity, explicit permissions, and continuous enforcement.
This model scales naturally from cloud workloads to service to service communication, APIs, and even machine identities in IoT deployments.
Users and groups as logical identity constructs
A core building block of IAM is the use of users and groups.
An IAM user represents a distinct identity, whether a human administrator, a developer, or an automated process. Groups act as logical containers for permissions, allowing policies to be applied collectively rather than individually.
This abstraction is important because it separates identity from permission logic.
At a higher level, this mirrors role based access control (RBAC) used in:
- Enterprise Active Directory environments
- Kubernetes RBAC
- Network device management systems
- Multi tenant research platforms
Instead of assigning permissions directly to individuals, access is derived from membership in roles or groups. This reduces configuration errors and improves auditability.
As systems scale, this pattern becomes essential for maintaining security and operational clarity.
Policies and least privilege enforcement
Policies define what identities are allowed to do. In AWS, these policies are expressed in JSON and explicitly specify permitted or denied actions on specific resources.
Every request is evaluated against:
- The identity making the request
- The attached policies
- Resource scope
- Explicit deny rules
This strict evaluation model reinforces the principle of least privilege, a concept that underpins secure system design across many domains.
Least privilege is foundational in:
- Secure network architectures
- Database access control
- API authorization frameworks
- Constrained IoT systems, where excess privilege increases attack surface
From a security perspective, misconfigured access policies remain one of the most common causes of cloud incidents. The issue is rarely the platform itself, but how permissions are designed and maintained.
This is why policy design should be treated as a core security discipline, not just a configuration task.
Multi Factor Authentication as a baseline control
Multi Factor Authentication (MFA) adds an additional layer of assurance beyond passwords or access keys. In AWS IAM, MFA can be enforced for privileged users and sensitive actions.
At a broader level, MFA is one of the most effective defenses against credential compromise. Whether applied to cloud consoles, enterprise VPNs, or administrative portals, it significantly increases the cost of attack.
MFA aligns closely with zero trust principles, where:
- No identity is implicitly trusted
- Authentication is continuously validated
- High risk actions require stronger verification
Across security research and real world incident analysis, lack of MFA remains one of the most preventable weaknesses in modern systems.
Programmatic access and the command line mindset
IAM is not limited to web consoles. Programmatic access through:
- The AWS CLI
- PowerShell
- CloudShell
is a fundamental part of operating securely at scale.
Using the command line reinforces an important mindset. Infrastructure and security controls should be automatable, auditable, and reproducible.
From a systems perspective, this connects directly to:
- Infrastructure as Code
- Policy as Code
- Secure CI and CD pipelines
Programmatic access enables consistent configuration, controlled automation, and traceable actions. In large scale environments, manual console operations do not scale. The terminal becomes the interface between policy, automation, and governance.
AWS security tools in a broader context
AWS provides a range of native security tools that integrate closely with IAM. While these tools are platform specific, the problems they address are universal.
Examples include:
- Identity monitoring and audit logging
- Configuration and compliance checks
- Threat detection and anomaly analysis
These capabilities reflect a broader shift toward continuous security monitoring rather than static controls.
From a research and systems standpoint, this mirrors trends seen in:
- Network intrusion detection systems
- Behavior based anomaly detection
- Telemetry driven security analytics
Modern security is not only about preventing access, but also about visibility, detection, and response when behavior deviates from expectations.
Connecting IAM to distributed and constrained systems
IAM principles extend well beyond cloud platforms.
In low power and distributed environments such as IoT, similar challenges appear:
- How to uniquely identify devices
- How to authenticate constrained nodes
- How to restrict device capabilities
- How to manage and rotate credentials securely
Although AWS IAM operates at a different scale, the conceptual model remains the same. Identities, permissions, and policy enforcement are central to securing distributed systems.
This overlap is where cloud security practice and systems research increasingly converge.
So the summary of all I have said is that IAM represents a foundational security model for modern computing. Identity-driven access control, explicit permission definition, least-privilege enforcement, strong authentication, and built-in auditability are not AWS-specific ideas, but core requirements that cut across cloud platforms, enterprise networks, and distributed systems. For anyone working in cloud, networking, or security, IAM is not a checkbox topic. It is a way of thinking about how secure systems are designed, operated, and scaled. Understanding IAM at this level provides value far beyond a single platform and establishes a strong foundation for more advanced work in cloud security and distributed system design.