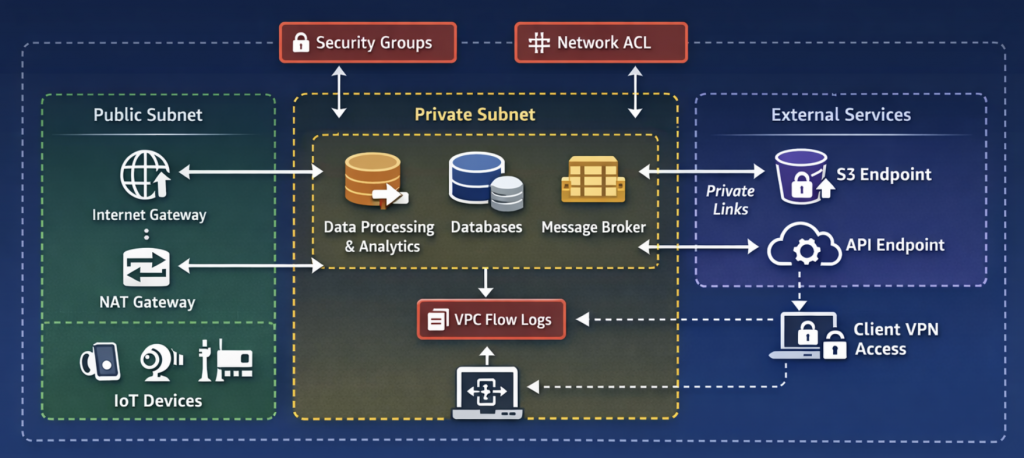
In cloud-based IoT architectures, networking is not a supporting detail but a foundational design decision. Before considerations around compute, storage, or analytics, the structure of the network determines how devices connect, how data moves, and how security boundaries are enforced. In Amazon Web Services, this foundation is established through the Virtual Private Cloud, which provides a logically isolated environment for building controlled, scalable, and security-aware IoT systems. A well-designed VPC enables precise segmentation of device traffic, backend services, and operational access, ensuring that growth in device count or data volume does not compromise reliability or trust.structed.
Within that VPC, subnets are not just a formality. They are the mechanism that separates public-facing components from protected internal services. In a typical IoT setup, internet-facing load balancers, device registration endpoints, or API gateways live in public subnets, while ingestion services, message brokers, databases, and analytics pipelines sit quietly in private ones. Internet gateways and NAT gateways then define directionality. Devices and field gateways may push data inward, but only carefully controlled components ever need to accept inbound connections. Outbound access for private resources, such as firmware update checks or external integrations, flows through NAT gateways without exposing internal addresses. This pattern becomes especially important in industrial or agricultural IoT, where long-lived devices should never be directly reachable from the public internet.
Security enforcement in this environment works best when it is layered. Security groups act as stateful guards around instances and managed services, expressing intent in terms of allowed communication paths rather than blanket access. Network access control lists add a stateless perimeter at the subnet level, which is useful for coarse-grained filtering and blast-radius control. Together, they reflect a defense model that aligns well with IoT realities: assume some devices will misbehave, constrain what they can talk to, and prevent lateral movement by default.
Visibility is the other half of control. VPC flow logs provide a network-level record of accepted and rejected traffic, which is invaluable when IoT traffic patterns change or anomalies emerge. In research-oriented IoT systems, these logs become a data source for understanding normal behavior, identifying misconfigurations, or even feeding anomaly detection pipelines. When combined with application logs and device telemetry, they help bridge the gap between network events and device-level behavior.
As IoT systems grow, they rarely stay confined to a single network boundary. VPC peering allows multiple VPCs to communicate privately, which is useful when separating environments by function, region, or trust level. A research testbed can peer with a production-like environment without collapsing isolation. VPC endpoints further refine this model by enabling private access to AWS services without traversing the public internet, which reduces exposure and simplifies compliance for sensitive data flows. For IoT workloads that rely heavily on managed storage, messaging, or analytics services, endpoints quietly improve both security posture and performance.
Operational access fits naturally into this same architectural model. Rather than exposing internal resources or relying on temporary workarounds, controlled mechanisms such as client VPN access allow engineers, researchers, and operators to interact with private IoT infrastructure in a secure and auditable way. In long-running IoT deployments, where teams evolve and experiments mature into production systems, this approach reinforces governance while preserving isolation. Viewed together, these networking components operate as a unified control plane rather than discrete services. They define how data enters the system, how it is constrained as it moves across trust boundaries, and how both machines and humans interact with the environment. When designed deliberately, VPC networking transforms an IoT platform from a loose collection of connected resources into a structured system where security, visibility, and scalability are intrinsic properties rather than retrofitted concerns.